

Demystifying Cloud Privilege Escalation and Lateral Movement




In the rapidly evolving landscape of cloud security, privilege escalation and lateral movement present significant threats that can compromise the integrity of your cloud environment. Cloud Security tools such as Cloud-Native Application Protection Platforms (CNAPPs) or Cloud Security Posture Management Platforms (CSPMs), are effective at identifying point-in-time vulnerabilities and misconfigurations, providing visibility into your inherent security risk posture. AiStrike complements these platforms - focusing on the investigation of real-time alerts and providing targeted response automation capabilities.
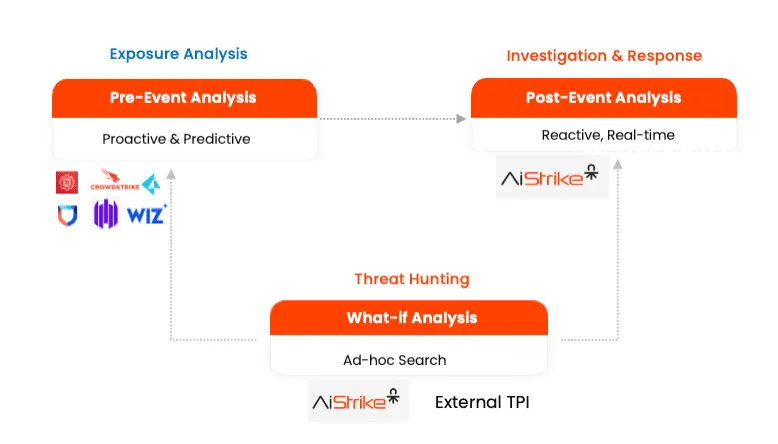
We don’t have to wait for a breach before the SOC begins preparation work—our tool handles that for the SOC. Cloud Exposure Analysis is highly valuable and can be done pre-breach. It's proactive work with several predictive capabilities. For example, we can calculate the path of least resistance that bad actors might take to access your crown jewels.
This work is also of great interest to IT, as we can prioritize vulnerabilities based not just on their CVE scores but on the actual assets within your organization and how they are connected. Cloud Investigation and Response represents the traditional work SOCs must do whenever an alert is triggered. It can be complex in the cloud due to its unique challenges. However, by conducting Cloud Exposure Analysis before a breach, cloud investigation and response become highly efficient. We gain deep insights into the alert, assets, identities, links, and risks, allowing us to validate, investigate, and respond swiftly. Additionally, we empower the SOC with capabilities to accelerate threat hunting, enabling them to conduct ad-hoc investigations efficiently.
AiStrike starts by collecting data related to cloud infrastructure, vulnerabilities, and misconfigurations. Beyond these standard sources, AiStrike also integrates with Cloud Infrastructure Entitlement Management (CIEM) systems to analyze access privileges and with Data Security Posture Management (DSPM) tools to identify assets holding sensitive or critical data.
Privilege escalation is often the key to enabling lateral movement within a cloud environment, allowing attackers to navigate closer to sensitive, crown jewel assets. AiStrike is engineered to map and detect possible privilege escalation paths that could potentially lead to crown jewels.
Our system proactively detects active escalation paths by continuously analyzing IAM permissions, roles, access keys, login profiles, and the misuse of cloud services like AWS PassRole, AWS STS, Azure Managed Identities, and Azure Role Assignments. AiStrike brings this level of sophistication to the cloud. By mapping out the shortest and most probable paths an attacker might take—whether through AWS IAM roles, Azure AD permissions, or GCP IAM roles—AiStrike ensures that no potential threat remains undetected.
We start from the compromised EC2 machine and trace a possible path using innocuous cloud native permissions / technologies to gain access to a sensitive S3 Bucket / database.

Beyond privilege escalation path detection, AiStrike enhances monitoring capabilities by leveraging AWS CloudTrail logs and Azure Activity Logs. These logs provide a detailed record of every action taken within your cloud environment, from role assumptions to policy changes. AiStrike continuously monitors these logs, tracing the complete session history of how roles are assumed, by whom, and tying these activities back to specific entities—whether an AWS EC2 instance, an Azure Virtual Machine, or a cloud IAM user in AWS or an Azure AD user.
By examining these logs, AiStrike can identify which users or entities have excessive permissions and determine which roles, policies, or managed identities could be exploited to access sensitive, crown jewel assets. This comprehensive analysis allows AiStrike to detect subtle patterns and anomalies that may indicate an ongoing attack, ensuring that your cloud environment remains secure.
AiStrike also leverages cloud infrastructure audit logs to create detailed timelines. These timelines visualize the sequence of events leading up to and following an alert, showcasing how roles were assumed, which permissions were used, and how access was granted or escalated. By consolidating this information, AiStrike provides a clear, actionable narrative that supports faster, more effective remediation.

Investigation is a critical step in securing your cloud environment. AiStrike complements the detections, vulnerabilities, and alerts provided by other systems by offering actionable insights that drive effective remediation. Once privilege escalation paths are identified, our platform pinpoints specific permissions, configurations, or sensitive assets that need immediate attention.
AiStrike doesn’t just identify risks—we automate the remediation process. By adjusting or removing risky permissions and addressing vulnerabilities associated with sensitive assets identified through DSPM, our platform proactively cuts off potential escalation paths before they can be exploited. This comprehensive approach ensures that your cloud environment remains secure, even as new threats continue to emerge.

AiStrike operates as a true Security Investigation and Response platform, complementing your CSPM and CNAPP tools. By continuously monitoring cloud activity, analyzing AWS CloudTrail logs and Azure Activity Logs, and integrating with CIEM/DSPM alerts, AiStrike provides a holistic view of your cloud environment’s security.
This comprehensive approach ensures that every potential threat vector is scrutinized, providing an unparalleled level of security that mitigates the risks associated with privilege escalation and lateral movement within your cloud environments.