Modern cybersecurity teams are overwhelmed by a relentless flood of alerts, each demanding attention. Investigating these in isolation not only drains analysts but also obscures the bigger picture—how individual alerts might connect to a broader, more sophisticated attack.
Threat actors like Black Basta exploit this lack of context, deploying advanced tactics that span multiple stages of the kill chain. To counter these threats, organizations need a smarter approach: one that prioritizes alerts and maps their progression across the kill chain to uncover relationships and true intent.
This blog explores how AiStrike leverages Composite AI and the MITRE ATT&CK framework to contextualize alerts, reduce fatigue, and empower analysts to stay ahead of complex threats like Black Basta.
Black Basta - Introduction
Black Basta, a ransomware group first identified in 2022, is experiencing a resurgence in 2024, continuing to pose significant threats globally. The group operates under a Ransomware-as-a-Service (RaaS) model, leveraging sophisticated tactics such as double extortion—encrypting data and threatening to leak sensitive information if the ransom isn't paid.
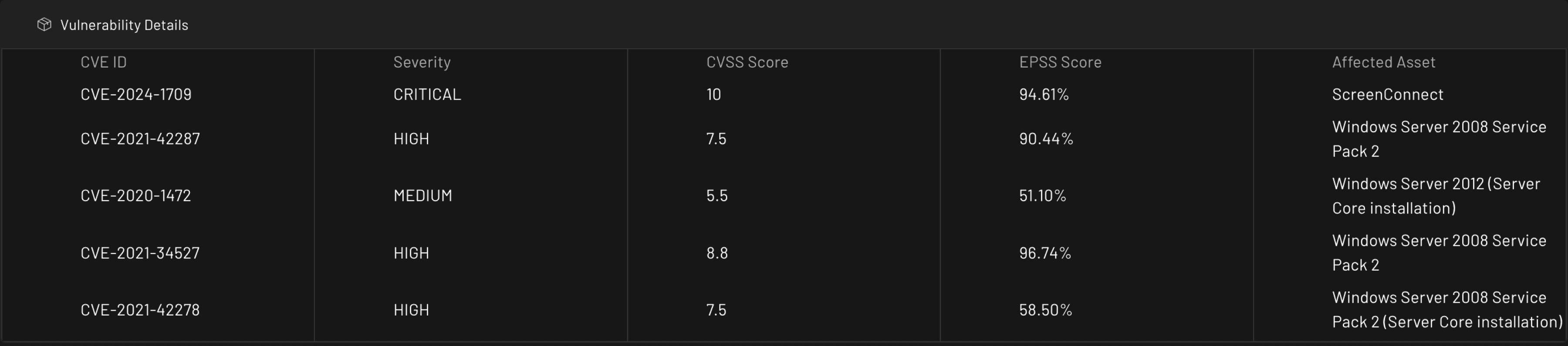
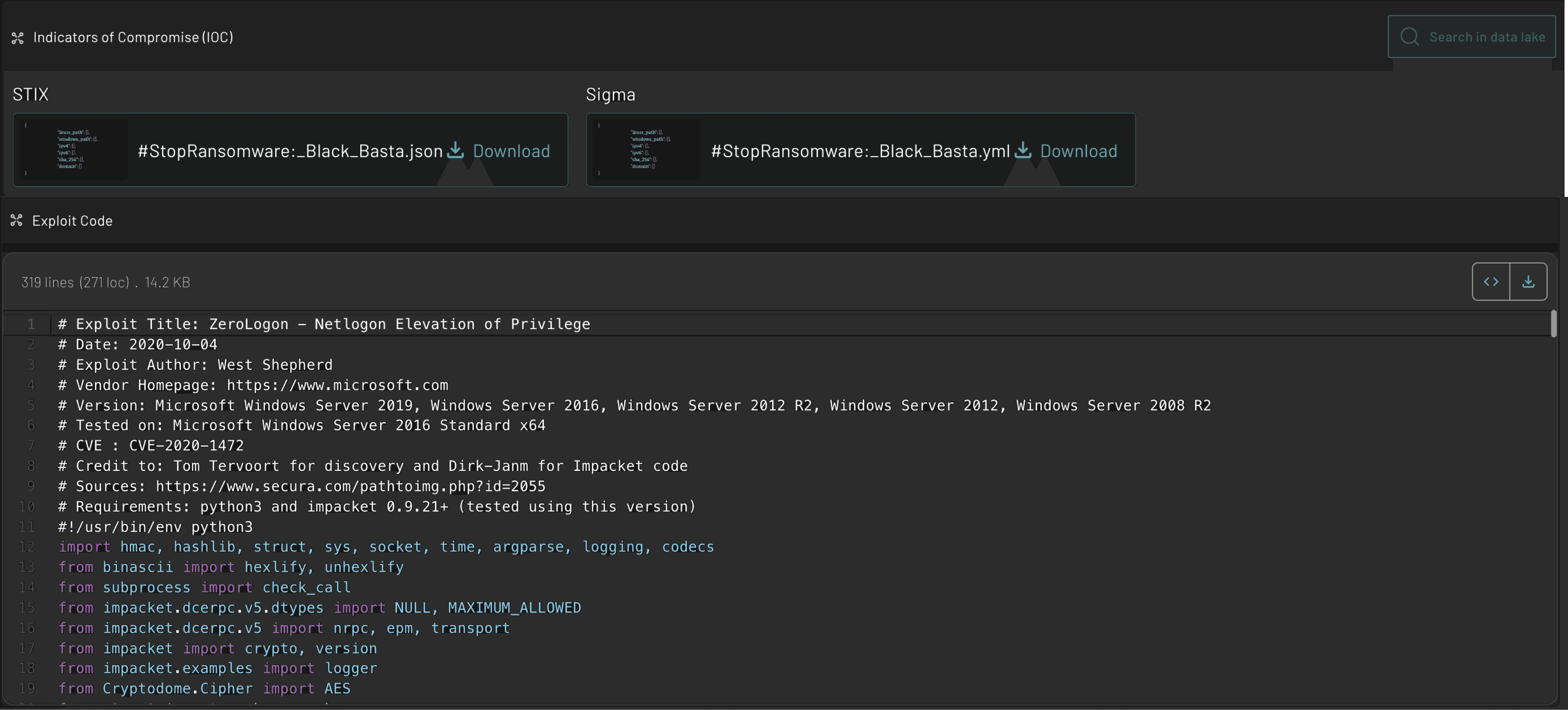
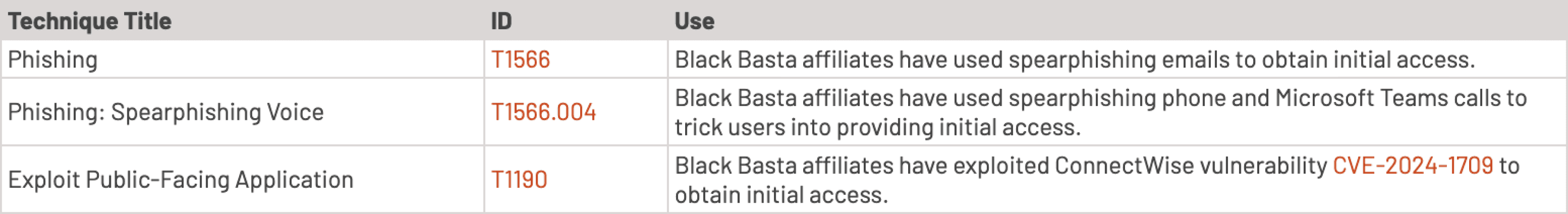
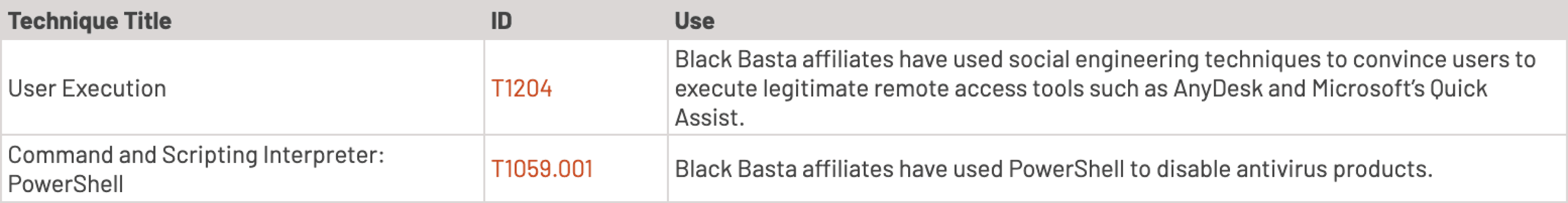
Recent activity demonstrates Black Basta's use of advanced tools and techniques, including exploiting vulnerabilities like CVE-2024-1709 and deploying tools such as Mimikatz and Cobalt Strike for privilege escalation and lateral movement. They also utilize spear-phishing campaigns and compromised remote access tools like AnyDesk to gain initial access. After infiltration, they disable defenses using tools like "Backstab" and encrypt systems with ChaCha20 and RSA-4096 algorithms. Indicators suggest increased operational activity in late 2024, with new infrastructure supporting their campaigns
The group’s resurgence underscores the importance of enhanced cybersecurity measures and vigilance against ransomware threats. More detailed indicators and mitigation strategies are available in the CISA advisory

Key Attributes and Threat Profile:
1. Geographic Focus and Targeting:
- Targeted countries: North America, Europe, Japan, Australia, and New Zealand.
- Targeted sectors: critical infrastructure, healthcare, and finance.
2. Threat Actors Aliases:
- Conti Ransomware: Black Basta is believed to have ties to Conti, evident from shared tactics, infrastructure, and code similarities.
- FIN7 (Carbanak): The group shares custom EDR evasion modules and command-and-control (C2) methods with FIN7.
3. Tools used:
BITSAdmin,Mimikatz,RClone,Splashtop,WMI,CobaltStrike,SoftPerfect,WinSCP,Mimikatz,Qakbot,
PowerShell,ScreenConnect,PSExec,EvilProxy,SystemBC,Backstab,Netcat,Quick Assist,NetSupport Manager
4. CVE Exploited:
CVE-2024-1709,CVE-2024-26169,CVE-2020-1472,CVE-2021-42278,CVE-2021-42287,CVE-2021-34527
Attack Lifecycle and Techniques:
Ref: https://www.cisa.gov/news-events/cybersecurity-advisories/aa24-131a
1. Initial Access:
2. Execution:
3. Privilege Escalation:

4. Defence Evasion

5.Impact:

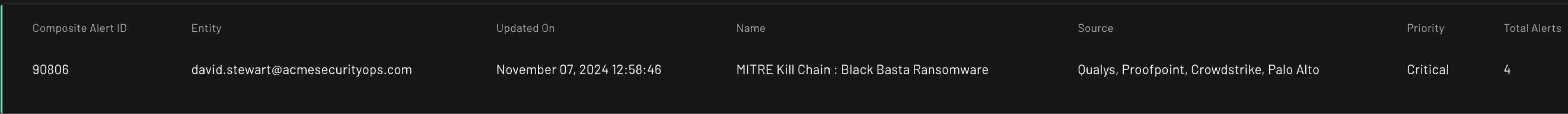
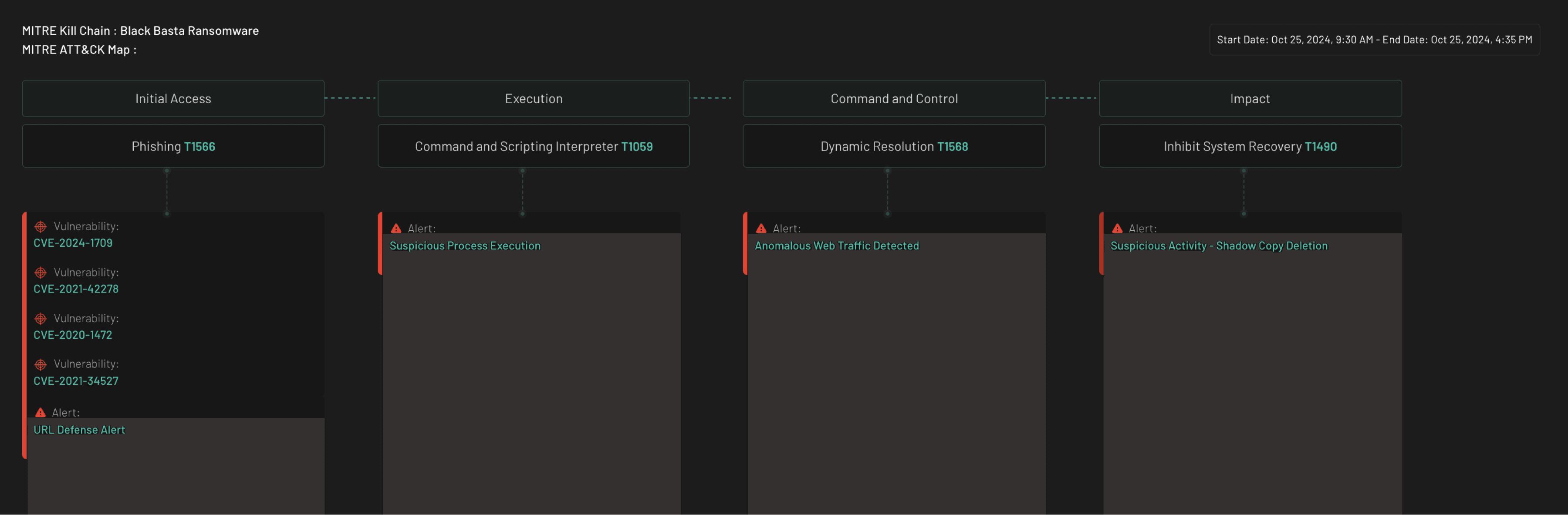
Mitre Based Grouping to detect Black basta :
In this scenario, our AI Agents are trained to successfully correlate multiple low-priority alerts into a high-risk threat, aligning with techniques outlined in the MITRE ATT&CK framework and indicating the presence of Black Basta ransomware activity.
The system effectively linked vulnerability data to our emerging threats database, which has been generated using LLM based AI agents, trained on over 10 years of threat campaign data. This AI agent leveraged the NER(Named entity recognition) to read and understand the details of the campaign, associating it with relevant alerts.
Sequence of Events :

Black Basta Context:
This pattern strongly aligns with Black Basta ransomware campaigns, where attackers leverage phishing for initial access, execute malicious payloads to establish C2, and deploy ransomware after disabling recovery options. The group’s use of sophisticated EDR evasion techniques and MITRE ATT&CK-aligned behaviors makes it a significant threat.
Additionally, AiStrike’s AI Copilot guides analysts through the investigation process, highlighting critical threat details and recommending pre-configured remediation actions built into the platform. Analysts can interact with the Copilot using prompts tailored to each alert type.
Conclusion:
At AiStrike, we harness the power of Composite AI to transform cybersecurity, enhancing defenses at every level. Our platform seamlessly integrates with enterprise security tools like SIEM, CNAPP, and XDR, ensuring compatibility and maximizing the value of existing solutions.
With AI-driven alert classification and automated investigations, AiStrike enables analysts to correlate events across diverse systems, uncover hidden patterns, and visualize complex relationships. This streamlines incident investigations, significantly reducing the time and effort required for effective threat response.
Our dynamic prioritization system, powered by an AI agent and machine learning classification engine, automatically correlates seemingly unrelated alerts as they progress through the kill chain. It performs behavioral analytics and analyzes network traffic patterns, such as robotic activity, impossible geotravel, rare events, or activity spikes, identifying common features and entities to deliver actionable insights.
By embracing Composite AI, organizations achieve unparalleled efficiency and precision in threat detection and mitigation, staying ahead of attackers. This innovative approach ensures smarter, more resilient defenses against the ever-evolving cyber threat landscape.




.png)
.webp)

.webp)
.webp)

.png)





.svg)
.png)